
|
DoorStop X Firewall User's Guide Configuration Tips |
 |

|
DoorStop X Firewall User's Guide Configuration Tips |
 |
This chapter discusses using DoorStop X to protect some commonly used network services, beyond the built-in protection -- often configurable via the Sharing Preferences pane -- afforded by each service. Since each section refers to DoorStop X's Setup window, a screen shot is included here:
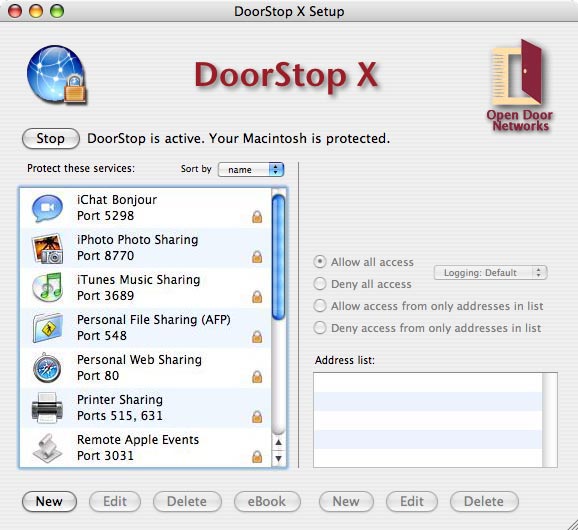
Figure 1. The DoorStop X Setup window
File Sharing (8, Personal File Sharing)
File Sharing allows you to share files on your Macintosh with other users on your intranet, or on the Internet. To enable File Sharing, go to the Sharing pane of System Preferences, click the Services tab, and check the box next to File Sharing. Users on other machines will be able to log into File Sharing on your Macintosh, using account names and passwords defined in the Accounts pane of System Preferences. For protection beyond that of user names and passwords, go to DoorStop's Setup window, choose File Sharing (port 548) from the list of protected services, and configure that entry to allow access from only those machines that need it. For example, if you wanted to allow access from other users on your local network, but not from the Internet, you could choose "Allow access from only addresses in list" and then make an address entry for your local subnet.
NOTE: "Back to My Mac" gives access to File Sharing without going through the standard File Sharing port. To protect File Sharing through Back to My Mac, you must protect UDP port 4500.
iApps and OS X's built-in firewall (9; 12, OS X's Built-in Firewall)
If you're going to use any of Apple's i-applications (iChat, iTunes or iPhoto) in conjunction with any firewall other than OS X's built-in firewall, you should first disable the built-in firewall. It's under the Security pane of System Preferences.
Configuring DoorStop X for iChat (9, iChat)
iChat is an extremely useful and popular application used for instant communication with other users, either on your local network, or on the Internet. iChat allows you to communicate via text, audio or video, to transfer files and to share your or others' screen. iChat operates differently depending whether you're communicating on the local network or the Internet.
iChat's many different modes, make it somewhat difficult to fully protect. When communicating with users on the Internet using text, iChat talks to an AIM (AOL Instant Messaging) server, which in turn relays your data to the distant user. When communicating with users on your local network, you can use OS X's Bonjour service to detect iChat-enabled machines on your network, and then communicate directly with those machines. For local communication, Bonjour is preferred to AIM, since your data is not exposed to the risks of the Internet. Audio, video and screen sharing, even over the Internet, use mainly peer-to-peer communcation as well, rather than going through the AIM server.
Further complicating things, iChat audio, video and screen sharing utilize UDP, and all three of these services utilize the same range of UDP ports.
Using iChat with AIM -- for text communication with users not on your local network, you don't need to configure DoorStop (as long as you don't block high-numbered UDP ports) unless you want to receive files through AIM/iChat's file transfer service. In that case, you need to allow the AIM server access to the "AIM (and iChat) File Transfer" service on port 5190 (or, more simply, just allow all access to that service). The service is listed in DoorStop's Service Information window.
Using iChat Bonjour, first you will need to confirm that Bonjour messaging is enabled. Go to iChat's preferences, click Accounts, and confirm that the account "Bonjour" has a checkmark next to it. If not, click the account name.
Second, you will need to configure DoorStop to allow all machines on your local network access to the built-in "iChat Bonjour" service (port 5298), listed in DoorStop's Setup window. If DoorStop is set to protect UDP, you also need to allow access from machines on your local network to:
iChat Bonjour seems to use a semi-random port number above 49151. You will need to check the DoorStop log file after access is attempted to determine exactly which port is being used, and then allow access as needed to that port.
Protecting iChat audio video and screen sharing, is somewhat complicated:
Due to iChat's complexity, you may well need to check Troubleshooting to try to figure out exactly what's going on.
Configuring DoorStop X for iTunes (9, iTunes)
Although iTunes is primarily an application for downloading, cataloging and playing music and video, it also has the (optional) ability to share music and video with other machines on your local network, including with an Apple TV device.
If you wish to prevent access from all machines on your network to iTunes on your machine, you should ensure that sharing in iTunes preferences (Figure 2) is disabled, and then confirm that DoorStop is set to deny access to iTunes from all IP addresses (this is DoorStop's default setting for iTunes).
If you wish to allow access from one or more machines on your network you must enable sharing in iTunes and then configure DoorStop to allow access to only those machines.
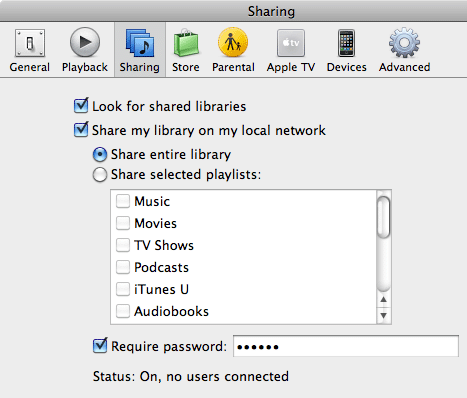
Figure 2. iTunes sharing preferences
To enable or disable the sharing of your iTunes files, check or uncheck the "Share my library on my local network" checkbox. If you check this checkbox, also check the "Require password" checkbox and enter a password. To configure DoorStop to allow access to one or more users, run the DoorStop application and, in the service list of the Setup window (Figure 1), select "iTunes Music Sharing/Port 3689". Next, on the right side of the Setup window, choose the desired protection, as described in Protecting a service.
Configuring DoorStop X for iPhoto (9, iPhoto)
iPhoto is similar to iTunes in that it is not primarily a networking application, but does have some optional local networking capabilities. As with iTunes, unless you want to actually share photos, you should not enable iPhoto's sharing capability, and should leave DoorStop's protection for iPhoto in its default state -- deny all.
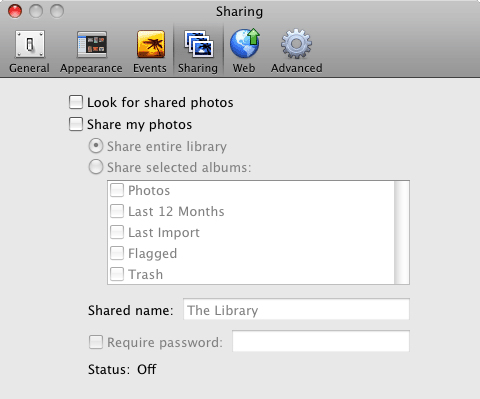
Figure 3. iPhoto sharing preferences
If you wish to share your photos with other users on your local network, check or uncheck the "Share my photos" checkbox in iPhoto's sharing preferences (Figure 3). If you check the "Share my photos" checkbox, also check the "Require password" checkbox and enter a password. To configure DoorStop to allow access to one or more users, run the DoorStop application and, in the service list of the Setup window (Figure 1), select "iPhoto Photo Sharing/Port 8770". Next, on the right side of the Setup window, choose the desired protection, as described in Protecting a service.
Configuring DoorStop X for Apple Remote Desktop/Management and Screen Sharing (8, Apple Remote Desktop, Screen Sharing)
Mac OS X includes a set of remote control and management technologies referred to collectively as Apple Remote Desktop (ARD). Apple Remote Desktop functionality has essentially been split into two pieces. The first, "Screen Sharing," lets another machine, running the Finder's Screen Sharing, remotely control your screen, mouse and keyboard (this screen sharing service is completely different from the one in iChat). The second, "Remote Management," is all the remaining Apple Remote Desktop remote management features. Each of these two pieces is enabled separately through Sharing Preferences.
DoorStop X 2.2 and later provide protection for the two pieces of ARD individually, regardless of which version of Mac OS X you are running. To provide access to remote control screen sharing functionality, use the "Screen Sharing/Remote Desktop" entry. To provide access to ARD's other features, use the "Remote Management/Desktop" entry. Note, however, if you are upgrading from a previous version of DoorStop X, only the single "Apple Remote Desktop" entry will be available, unless you delete it and add the other two back.
NOTE: "Back to My Mac" gives access to Screen Sharing without going through the standard Screen Sharing port. To protect Screen Sharing through Back to My Mac, you must protect UDP port 4500.
Configuring DoorStop X for Internet Sharing (8, Internet Sharing)
Mac OS X includes Internet Sharing, the ability of a Macintosh to share its Internet connection with other computers. Say, for example, that your Mac at home is connected to a cable modem, and that you wish to share that Internet connection with a wireless Mac in your home. Go to the Sharing pane of System Preferences to see the pane shown in Figure 4. Click the Internet Sharing checkbox in Figure 4 to share the wired Internet connection of your machine with other computers via AirPort.
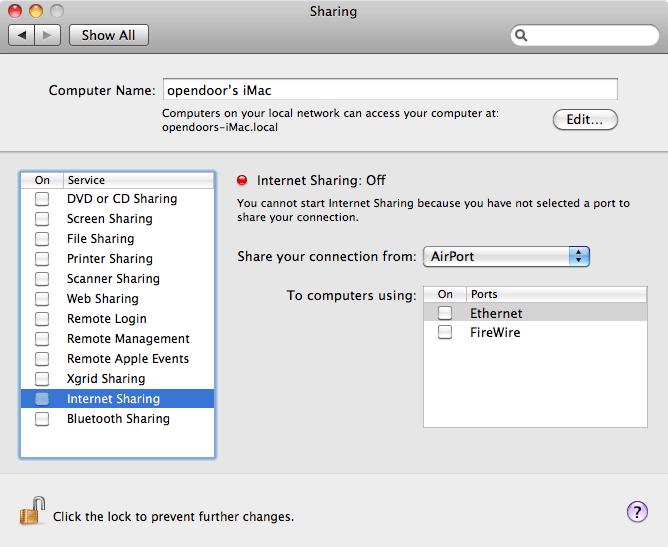
Figure 4. Internet Sharing preferences
To use Internet Sharing with a firewall running on your machine, however, requires a few more steps. Note that this pertains to any firewall, not just DoorStop. If client machines sharing your Internet connection wish to access the Web, you must enable your firewall to allow access to Web Sharing. You do not need to enable Web sharing on your machine, just access to Web Sharing's port (80) in the firewall on your machine. Likewise, if a client machine wishes to read and send email, you must enable the firewall on your machine to allow access to POP (Post Office Protocol) and SMTP (Simple Mail Transfer Protocol), for receiving and sending mail, respectively. For maximum security, allow access to these ports only from the shared network range (for instance 192.168.2.0 - 192.168.2.255). Some of the services that clients use may be in DoorStop's built-in services, and other may need to be defined by you. Protecting built-in services is covered in Protecting Basic Services, while protecting user-defined services is covered in Protecting User-defined Services.
FTP clients (14, What is FTP?)
You should be able to connect to many FTP servers without configuring DoorStop. Some FTP clients or servers, however, may use a feature of the protocol which works by having the FTP server open a TCP connection back to your machine and then use that connection as a "data port", to get data from your machine. The problem is that a) the port number used for the data port is usually picked more or less at random, and b) the FTP server must have access to the data port it decides to open on your machine. There are a number of options for enabling such access:
![]() Back to Table of Contents
Back to Table of Contents
![]() Back to User-defined Services
Back to User-defined Services
![]() Forward to Accessing the Book, the Blog & Twitter
Forward to Accessing the Book, the Blog & Twitter