
|
Who's There? Firewall Advisor User's Guide Appendices |
 |

|
Who's There? Firewall Advisor User's Guide Appendices |
 |
Mac OS X's built-in firewall (12)
Mac OS X 10.4 and later include logging capabilities with their built-in firewall user interface, accessible through the System Preferences window. The Leopard log file contains insufficient information to be useful to Who's There? in any way, and Snow Leopard's log file is in a non-standard format; neither of these built-in firewalls is supported. The Tiger log file is supported with the following significant caveat:
SECURITY WARNING: In Tiger, the firewall log only includes denied connection attempts. If any access attempts to your machine (desired or otherwise) are successful, these attempts will not be included in the log. Due to its lack of logging of successful access attempts, Open Door recommends against use of Tiger's built-in firewall user interface.
An additional, although much less severe, problem with logging in Tiger's built-in firewall user interface is that Mac OS X archives and resets the log file every 7 days, and deletes old archived logs after approximately a month. Thus, in addition to not being able to analyze successful access attempts at all, Who's There? can only analyze at most the last week's worth of denied access attempts through Tiger's built-in logging.
If you choose to use Tiger's built-in firewall, go to System Preferences and choose Sharing. In the Sharing window, click on the Firewall tab to display firewall settings (Figure 1).
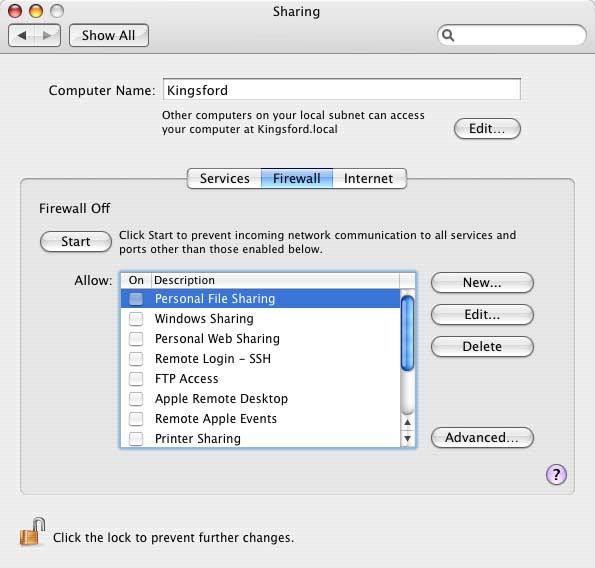
Figure 1. Firewall settings
Choose the services, if any, for which you want to allow access, and then click the Start button. Next, confirm that firewall logging is enabled by clicking the Advanced ... button and check Enable Firewall Logging (Figure 2).
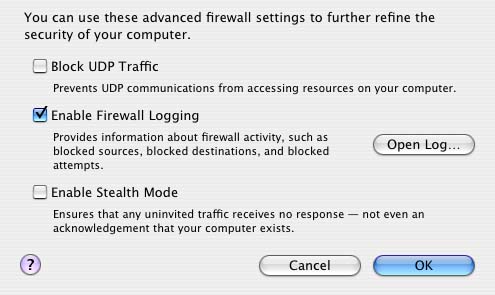
Figure 2. Firewall advanced settings
TCP and UDP Port Numbers Commonly Used by Macintosh Services (6, Port Numbers)
For the latest information on port numbers, see the list on our Web site.
Who's There? and routers (15, Home Routers)
Home routers, including wireless access points like the Airport Base Station, are used more and more in small networks as a way to share an Internet connection. By their nature, such routers provide some protection from access attempts from the Internet. In fact, unless a home router is specifically configured to do otherwise, no attempts from the Internet to access services on machines behind a router will succeed. This brings up a number of points:
Log File Formats (12, Features)
To be processed by Who's There?, your firewall's log file must be written in one of the three supported formats. These formats are:
Mac OS X ipfw log format (system.log, WhosThere.log and ipfw.log)
Fields are space-delimited.
Log lines in OS X ipfw log format look like this:
| Jan | 30 | 17:28:45 | localhost | mach_kernel: | ipfw: | 303 | Deny | ICMP:8.0 | 192.168.0.1 | 192.168.0.2 | in via en0 |
| Jan | 30 | 17:28:48 | localhost | mach_kernel: | ipfw: | 10001 | Deny | UDP | 192.168.0.2:49161 | 239.255.255.253:548 | in via en0 |
Notes:
Extended WebSTAR log format
Operations are logged using the following tokens (which are included in the !!LOG_FORMAT line whenever your firewall starts up or a new log file is written):
Actions related to the firewall itself are logged using the standard WebSTAR comment format:
!!LOG_FORMAT DATE TIME RESULT HOSTNAME SERVER_PORT METHOD
!!ENABLE_LOGGING 05/19/00 16:34:07
!!DISABLE_LOGGING 05/19/00 16:34:15
!!ENABLE_FILTERING 05/19/00 16:34:24
!!DISABLE_FILTERING 05/19/00 16:34:23
Log lines in extended WebStar format look like this:
!!LOG_FORMAT DATE TIME RESULT HOSTNAME SERVER_PORT METHOD
05/19/05
16:52:19
ERR!
192.0.0.2
21
TCP
05/19/05
16:52:39
OK
192.0.0.2
21
TCP
05/19/05
16:52:39
OK
192.0.0.2
2051
UDP
Operations are logged using the following tokens (which are included in the !!LOG_FORMAT line whenever your firewall starts up or a new log file is written):
Actions related to the firewall itself are logged using the standard WebSTAR comment format:
!!LOG_FORMAT DATE RESULT HOSTNAME SERVER_PORT METHOD DIRECTION
TYPE
!!04/30/2003 11:16:22 -0700 ENABLE_FILTERING
!!05/06/2003 12:08:26 -0700 DISABLE_FILTERING
Log lines in extended NPF 3 format look like this:
!!LOG_FORMAT DATE RESULT HOSTNAME SERVER_PORT METHOD DIRECTION
TYPE
05/06/2005 12:06:55 -0700
OK
192.0.0.2
49161
UDP
IN
User
05/06/2005 12:04:45 -0700
ERR!
192.0.0.2
548
TCP
IN
User
05/06/2005 11:52:15 -0700
OK
192.0.0.2
8
ICMP
IN
Stealth Mode
Note that the TYPE token is ignored by Who's There?