
|
Who's There? Firewall Advisor User's Guide Other Windows |
 |

|
Who's There? Firewall Advisor User's Guide Other Windows |
 |
This chapter assumes that you are familiar with the material presented in Basic Concepts.
To set Who's There? preferences, choose "Preferences" from the Who's There? menu. The preferences dialog, shown below in Figure 1, can be viewed in two panes: General and Display. Choose the pane you want by clicking the corresponding icon. The General pane is used to specify two items: the log file to be processed, and the email template. Each is discussed in a separate section below.
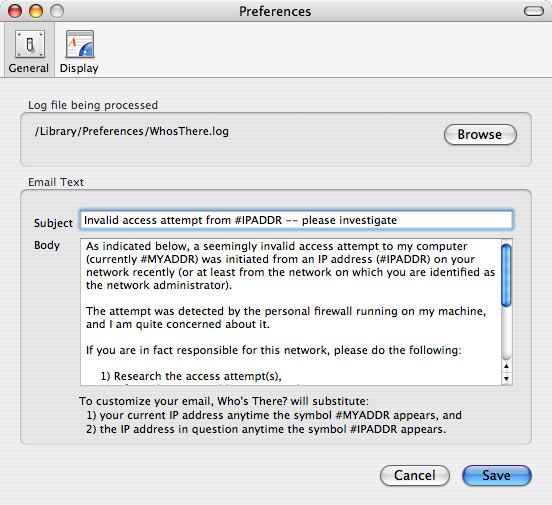
Figure 1. General preferences
Who's There? can process firewall log files in one of three formats:
Logging firewalls using OS X's built-in firewall technology ("ipfw") write to a log file, the name, location and format of which depend on the version of OS X you're using and how the firewall uses ipfw. NOTE: Mac OS X 10.5's built-in firewall does not use ipfw technology and is not supported.
To a point, the more information a log file contains, the more useful Who's There? becomes, due to patterns and trends in access attempts possibly becoming clearer. However, all log files created by ipfw are automatically rolled (archived and then cleared) by OS X (daily or weekly, depending on the version of OS X). When a log file is rolled, all access information prior to the moment of rolling becomes unavailable to Who's There, making Who's There? somewhat less useful. If you're using DoorStop X (part of the DoorStop X Security Suite), this is not a problem, because DoorStop tells OS X to write ipfw lines to the default location, AND to a separate log file that is not automatically rolled by OS X (but can be set to roll automatically within the DoorStop application). If you are not using DoorStop X, but rather another ipfw-based firewall, it may be possible to prevent Mac OS X from rolling the log file. Contact Open Door Networks directly for details.
When launched, Who's There? will look for a log file to process, in this order:
If Who's There? cannot find one of the above log files, you will be given the option of locating a log file (below).
Lines in OS X's ipfw log format do not include the year of the access attempt. When reading a line from WhosThere.log (or ipfw.log), Who's There? assumes the current year. If this results in a date ahead of the current date, Who's There? subtracts 1 from the year. This means that log files containing data over one year old will result in that data being shown in either the current or previous year, but no earlier than that. For this reason, it is recommended that you archive the log file at least once a year. The DoorStop X firewall provides ways of doing this automatically, manually or using AppleScript; other firewalls may provide different facilities.
Choosing another log file
Once Who's There? has started up, you can specify a different log file for processing in two ways:
Be sure that the file you locate is a firewall log file in the correct format -- other text files will be opened, but will display no data. Note that if you choose a log file generated by a firewall on another machine, the advice presented by Who's There? will only be accurate if the other machine is running a similar version of OS X. The security risks of OS X differ from those of other operating systems.
You can also override the default log file that Who's There? is set to process when it runs. To do this, hold down the option key when running Who's There? You will be presented with the log file Browse dialog, from which you can choose a new log file. That log file will be processed and then become the default until you change it.
The template used to create an email draft is displayed in the section labeled "Email Text". When an email draft is created, the "Subject" and "Body" fields of the template are inserted in the corresponding fields of the draft, with the following changes:
The actual email draft also includes up to 100 sample log lines, inserted after the template text. Also, lines are added at the end of the email, one of which refers to the time zone of the machine running Who's There. Be sure, using the Date & Time System Preferences dialog, that the Time Zone setting is correct.
The Display pane of the Preferences dialog (Figure 2) is used to specify items displayed in the Access History window and how they are displayed. Except as noted, these settings affect only the Access History window, and not the Summary by IP Address or Summary by Service windows. Each item is discussed in a separate section below.
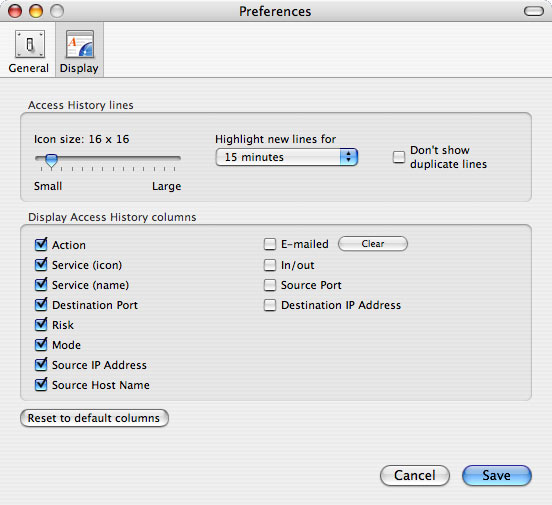
Figure 2. Display preferences
Icon size
The service icons displayed in the Access History window are 16 x 16 pixels by default. If you wish to change the icon size, use the "Icon size" slider. For small icon sizes, the text size will be changed, too.
Highlight new lines
By default, Who's There? highlights (with bold type) new lines in the Access History window (and the two "Summary by ..." windows) until they're 15 minutes old. You can change that period with the "Highlight new lines for" popup menu.
By default, the Access History window displays all log lines that match the filter criteria. For doing certain types of log file analysis, you may find it useful to eliminate duplicate log lines. That is, if there are 500 lines for incoming access attempts from IP address 192.168.1.103 to port 80 on your machine, you may wish to see only one log line for that combination of accessor IP, port number and direction on your machine. To do this, check the "Don't show duplicate lines" checkbox. You will see only one log line for any set of adjacent lines where each line is an identical combination of
Columns
The default columns displayed in the Access History window are the ones checked in Figure 2. If you wish, there are additional columns you can have Who's There? display, by checking the appropriate checkbox.
You can return the columns settings to their default values by clicking the "Reset to default columns" button. Note that all columns, even those not displayed, can still be filtered on using the Access History window's filter field.
Lookup IP address (6, IP Addresses and Host Names)
To get information on any IP address, regardless of whether it appears in your firewall's log file or not, use "Lookup IP Address..." in the Edit menu to bring up the Lookup dialog, shown below in Figure 3. Enter the IP address and click the Lookup button or hit the Return or Enter key. The Who's There? dialog will appear, displaying the appropriate information.
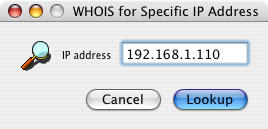
Figure 3. Lookup dialog
Online Help
Online help is available in two ways:
Either method will invoke online help for Who's There, which is structured much like this User's Guide.
![]() Back to Table of Contents
Back to Table of Contents
![]() Back to Who's There? Dialog
Back to Who's There? Dialog
![]() Forward to Accessing the Book, the Blog and Twitter
Forward to Accessing the Book, the Blog and Twitter