
|
Who's There? Firewall Advisor User's Guide Who's There? Dialog |
 |

|
Who's There? Firewall Advisor User's Guide Who's There? Dialog |
 |
This chapter assumes that you are familiar with the material presented in Basic Concepts. This chapter describes the Who's There? dialog, shown in Figure 1 below. The dialog presents detailed information on IP addresses or services selected in the main window. When a data item in the main window is selected and an action button clicked, the Who's There? dialog appears with detailed information on the data item.
This dialog can present up to four kinds of information, controlled by the tabs at the top of the window:
Not all tabs will always be active. The active tabs correspond to the active action buttons in the main window.
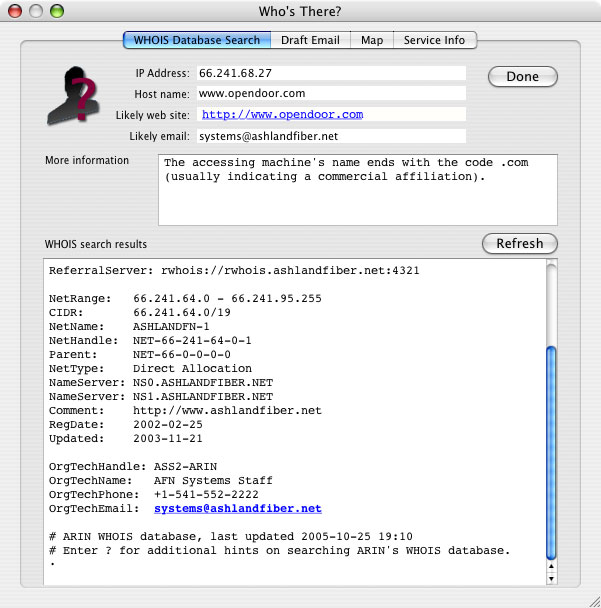
Figure 1. Who's There? dialog
This tab displays information regarding the network on which the machine attempting the access resides. See Figure 1 above.
This information is obtained by using an Internet technology called WHOIS, which is a distributed database maintained by different authoritative agencies. The information contained in WHOIS is generated from the registration of domain names, and the allocation of IP address blocks by authoritative Internet agencies, such as IANA (Internet Assigned Numbers Authority). Most end users are not allocated IP addresses from an authoritative Internet agency, but are assigned them by their ISP. In fact, many ISPs do not guarantee that a given user will get the same IP address every time they connect to the Internet. For these reasons, the WHOIS search will often not yield information about the end user who attempted access to your firewall machine; information often ends with the user's ISP.
Note that Who's There? does not generate the information, it merely presents what is returned from the WHOIS databases. Because these databases are not maintained by Open Door Networks, their accuracy cannot be guaranteed, although the information is generally correct.
Certain information is displayed in the top pane of the dialog:
Who's There? always begins its search with ARIN (American Registry for Internet Numbers). If that database does not contain information on the requested IP address, the search is redirected to other WHOIS databases. Also, if the results from one search suggest more specific information elsewhere, the search is redirected to that information. For this reason, information tends to get more specific as the search continues.
The results of the WHOIS lookup are displayed in the lower pane. The results of the search of each WHOIS database are marked with a line that begins "Looking up" in bold black. As you scroll farther down the lower pane, successive database searches will give more specific information about the administrator of the accessor's network, such as physical address, phone number and email address. Note that email addresses are in bold blue. Clicking an email address will cause the address to be added (if it's not already there) to the email recipient list in the Likely email field in the top pane of the dialog. See Figure 2 below.
It is recommended that you limit your first email to one email address. If that address does not get you to the right administrator, you can use other addresses in subsequent emails. Addresses should usually be chosen starting from the bottom of the dialog, since information toward the bottom tends to be more specific than at the top. Alternatively, you can attempt to contact a network administrator using other WHOIS information, such as their phone number or mailing address
This tab displays the draft of an email to the likely contact for the accessor's network. See Figure 2 below.
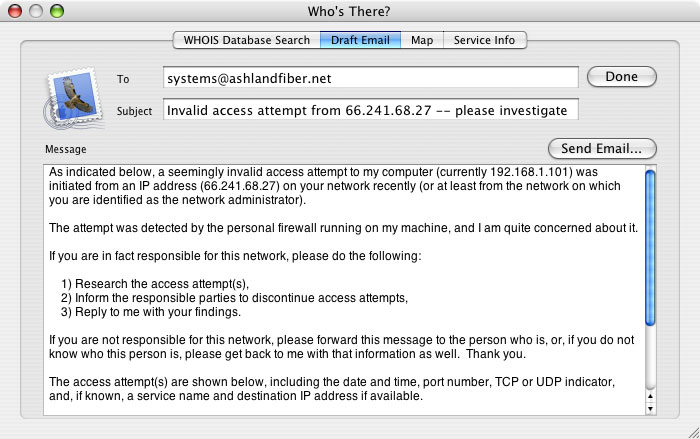
Figure 2. Draft email
The email draft uses the email template stored in Who's There's preferences as follows:
The "To", "Subject" and "Message" areas of the email draft can be edited. The "Send Email..." button is used to create an actual email, using your machine's default email application. To specify a particular email application, see the relevant troubleshooting item.
When the "Send Email..." button is clicked, the information in the email draft is passed to your default mail application. The email is not automatically sent, however. You can use the email application itself to further edit the email, and then to actually send it as desired. Clicking the "Send Email..." button also causes the Emailed column in the Access History window to be checked for each relevant log line currently displayed. Note that Who's There? only includes the first 100 lines displayed for a given IP address, but will check all such lines. If lines in the log file are not displayed in Who's There, due to data filtering, those lines will not have checkmarks if they are later displayed,
As stated in the section above on WHOIS lookups, the data presented by Who's There? cannot be guaranteed to be accurate. This includes email addresses, which may be misspelled or out of date. If an email is returned as unsendable, look in the WHOIS window, starting at the bottom, for other email addresses to try, or contact the network administrator using other WHOIS information, such as phone number or mailing address.
NOTE: The IP address you investigate may or may not be the origin of a given attack. A common ploy used by hackers is to use others' machines to launch their attacks from. Since this is done without a user's knowledge, a user you investigate may rightly claim to have no knowledge of the attack. If this occurs, you may wish to suggest to them that their machine may be infected with a virus or otherwise have been taken over by a third party.
The blue cursor shows the geographic location associated with the accessor's IP address. See Figure 3 below.
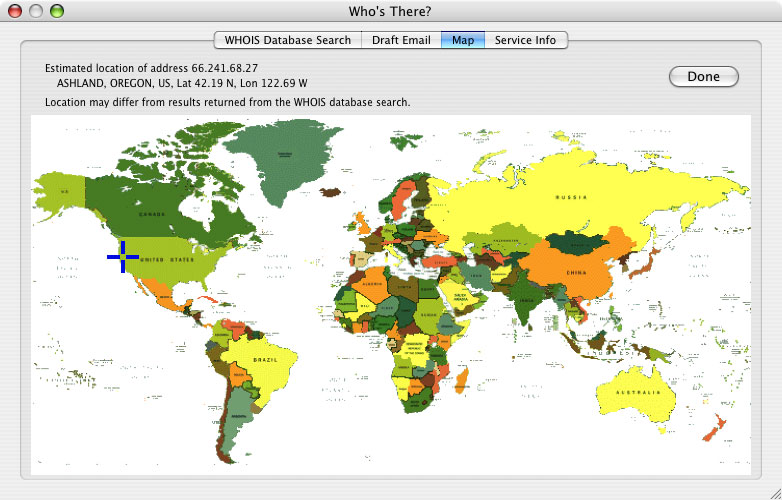
Figure 3. Map
Who's There? uses an Internet service to look up the accessor's IP address and obtain latitude and longitude values, which are then used to place the cursor on the map. The city and country, along with latitude and longitude values, are displayed at the top of the dialog. Note that the geographic location shown may not match the location specified in the WHOIS lookup, since the map data and WHOIS data come from separate sources, neither of which has guaranteed accuracy.
This tab displays information about a service, if known. See Figure 4 below.
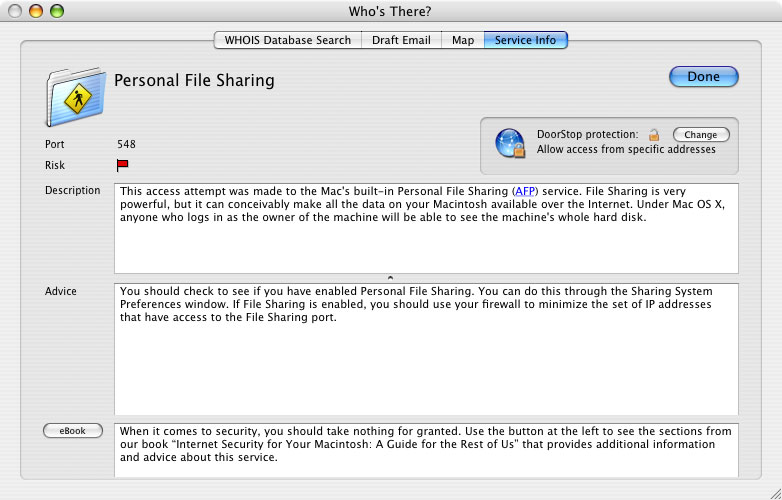
Figure 4. Service info
Information includes:

Figure 5. eBook entries on port 548
A list of relevant passages is displayed on the left, with the text of passages displayed on the right. If there is nothing in the book that corresponds to a service, you'll see a list of passages that relate to unknown services. You can also search the book's blog, isfym.com, and Top 10 list for current information on the service; or visit our Twitter stream (twitter.com/isfym) for even more up-to-date information.
![]() Back to Table of Contents
Back to Table of Contents
![]() Back to Main Window
Back to Main Window
![]() Forward to Other Windows
Forward to Other Windows